Hardware Trojans
The Integrated Circuits (IC) design supply chain has become vulnerable to the insertion of malicious hardware like Hardware Trojans, due to third parties’ intervention, which are not always reliable.
A Hardware Trojan (HT) is a material intrusion or modification of the original hardware design, that affects the trustworthiness of an electronic system, even in consumer electronics. It is therefore important to ensure the hardware security of IC devices.
Hardware Trojans’ threat in IC supply chain
To reduce the cost of IC in terms of time and money, designers outsource some manufacturing steps. Third parties that may be involved during the outsourcing process could potentially introduce the initial design to make malicious modifications.
The threat of Hardware Trojans insertion is present at any phase of IC manufacturing, and has become a real problem for ICs. It can have serious consequences such as leakage of sensitive information, function modification, data modification or data theft, counterfeiting etc.; especially in some critical application areas such as military, IoT, banking, healthcare and so on. Thus, the presence of Hardware Trojans could really affect the reliability of a design. It is therefore important to be able to detect them.
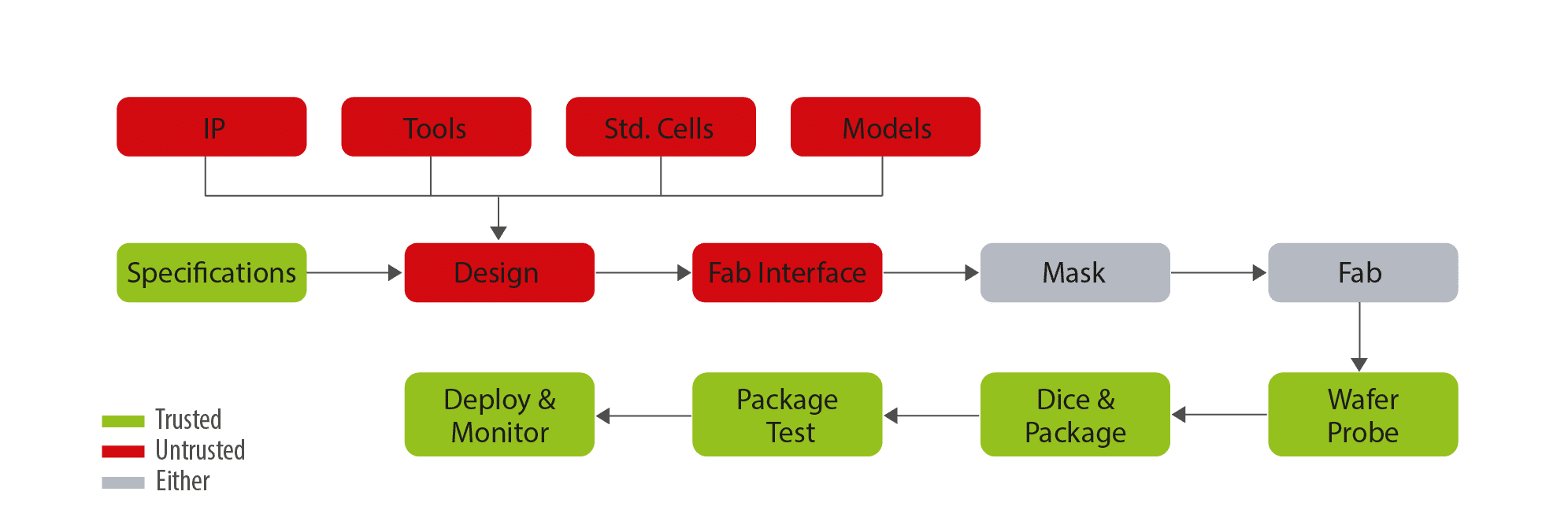
The following figure from Chakraborty and al., shows the degree of confidence in each IC design steps. The insertion can occur from the RTL design phase to the manufacturing phase.
Hardware Trojans prevention and detection
For example, among the post-silicon detection methods, that is to say after IC manufacturing, there are logical test methods, side-channel analysis methods based on the analysis of the physical parameters (delay, energy consumption, electromagnetic emanations, etc.) of the ICs. These physical parameters will be modified due to the insertion of Hardware Trojans, and their analysis will therefore allow to detect their presence.
Regarding all of this, one of Secure-IC’s missions is to prevent and detect Hardware Trojans insertions from IC of electronics devices. That is why we offer evaluation tools with LaboryzrTM to assess the weaknesses of a system against Hardware Trojan threats. It offers Side Channel Analysis, reactive analog detection or machine learning, allowing to detect and deal efficiently with Hardware Trojans insertion.
Secure-IC also provide protection and detection IPs which implement proactive and reactive methods with Cyber Escort UnitTM and Digital SensorTM combined with Secure-IC’s AI-based security monitoring technology Smart MonitorTM.
LaboryzrTM
Cyber Escort Unit IP
Digital Sensor IP
Smart Monitor IP
Related Resources & Events
You may also be interested in having a closer look at the elements below:

U.S. Media “Cyber Defense E-Magazine” publishes Secure-IC’s insight on Hardware Trojans Detection

Hardware Trojans or the Threat of Malicious Circuits