Cybersecurity Evaluation Tools
How to ensure that your devices are secure against cyber-attacks and do not present any potential vulnerabilities? Security evaluations allow to determine clearly the degree of compliance of your devices to a specific security model or a targeted security standard.
Facilitate your security evaluation with specifically designed risk assessment tools.
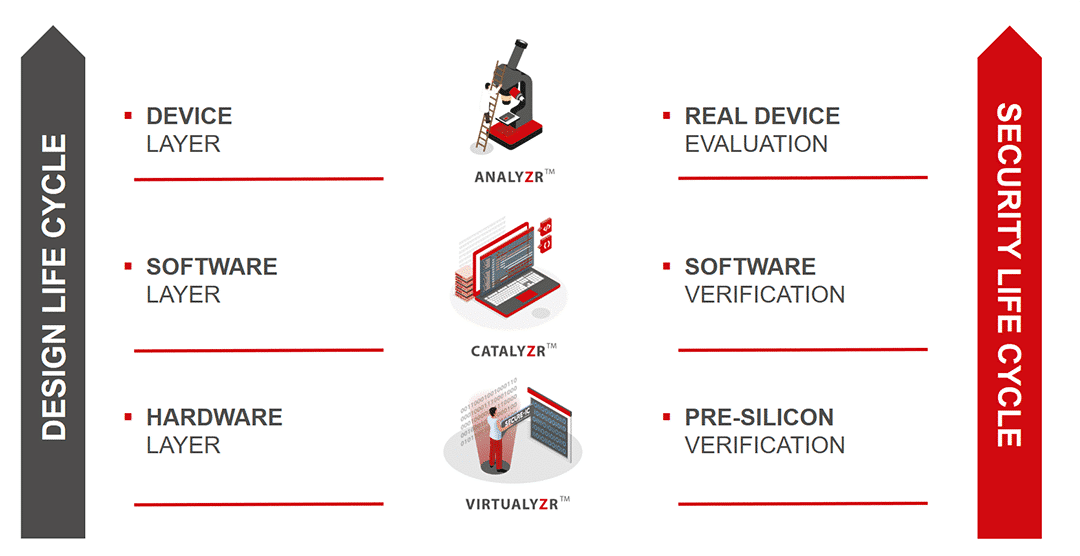
Risk assessment is one of the most important steps in the design life cycle; this is why security needs to be present on each level of the design, whether it be during the pre-silicon stage, all the way to the finished product stage.

Security for each stage of the evaluation
- Pre-silicon:
Since there is no need to produce chips, evaluation costs are reduced. It also increases confidence before starting the production of a chip. - Post-silicon:
Testing chips to ensure the level of security.
Chip evaluation is an important step in design and production
- Pre-testing is requested for some certifications.
- Add value to your system by evaluating it.
A tool for each stage of the evaluation
Secure-IC offers to evaluate your full design process, from pre-silicon, thanks to a dedicated evaluation and security tool called LaboryzrTM.
Security Evaluation had never been easier with the associated set of tools that have been designed specifically for risk assessment all along the life-cycle of a product.


LaboryzrTM covers both classes of analysis and more:
- Passive: Side-channel analysis
- Active: Fault injection analysis
- Hardware Trojan Detection
- Reverse Engineering prevention
Secure-IC can provide a wide range of security services through the design life-cycle; based on three main tools
- Control the potential physical leaks
- Check the compliance level of your chips
- Ready-to-use evaluation laboratory
- Perform side-channel (SCA attacks) and fault injection (FIA attacks) measurements and analysis
- Security validation
- Offensive testing to verify the integrity of the security
- Software security verification layer
- Control-flow, Data-flow analysis and Fault-analysis
- Design for Security from the first source code of IP toward SoC layout just before going to foundry. It provides a security verification layer that runs hand in hand with functional verification workflow
- Allows performing security checkpoints at different design levels
- Detects and characterizes the security vulnerabilities from the design
- Maps the vulnerabilities with the design
- Cheaper evaluation as no measurement equipment or platform is required.
- Evaluation of mixed design: Both Hardware and Software
Our team of experts can provide advice on appropriate threat protection and on chip characterization of the level of resistance of our products against attacks.
Fully compliant Evaluation to standard certifications
Secure-IC supports its customers reach their desired certification levels with general certifications such as Common Criteria, FIPS-140 or OSCCA; but also to reach their target in more specific standards such as ISO/IEC 17825 or 20085.