THE FIRST WORLDWIDE PQC READY SECURE SOLUTION FROM CHIP TO CLOUD
At Secure-IC we are at the forefront of PQC, meaning we are actively working on developing and implementing PQC technologies, and contributing to the advancement of the field. We are conducting research, creating new PQC algorithms, developing PQC-based products, and working with customers to integrate PQC solutions into their systems.
We have the expertise, experience, and resources to help shape the future of secure communications in a world where quantum computing is increasingly prevalent.

Secure-IC has several IPs that are PQC ready
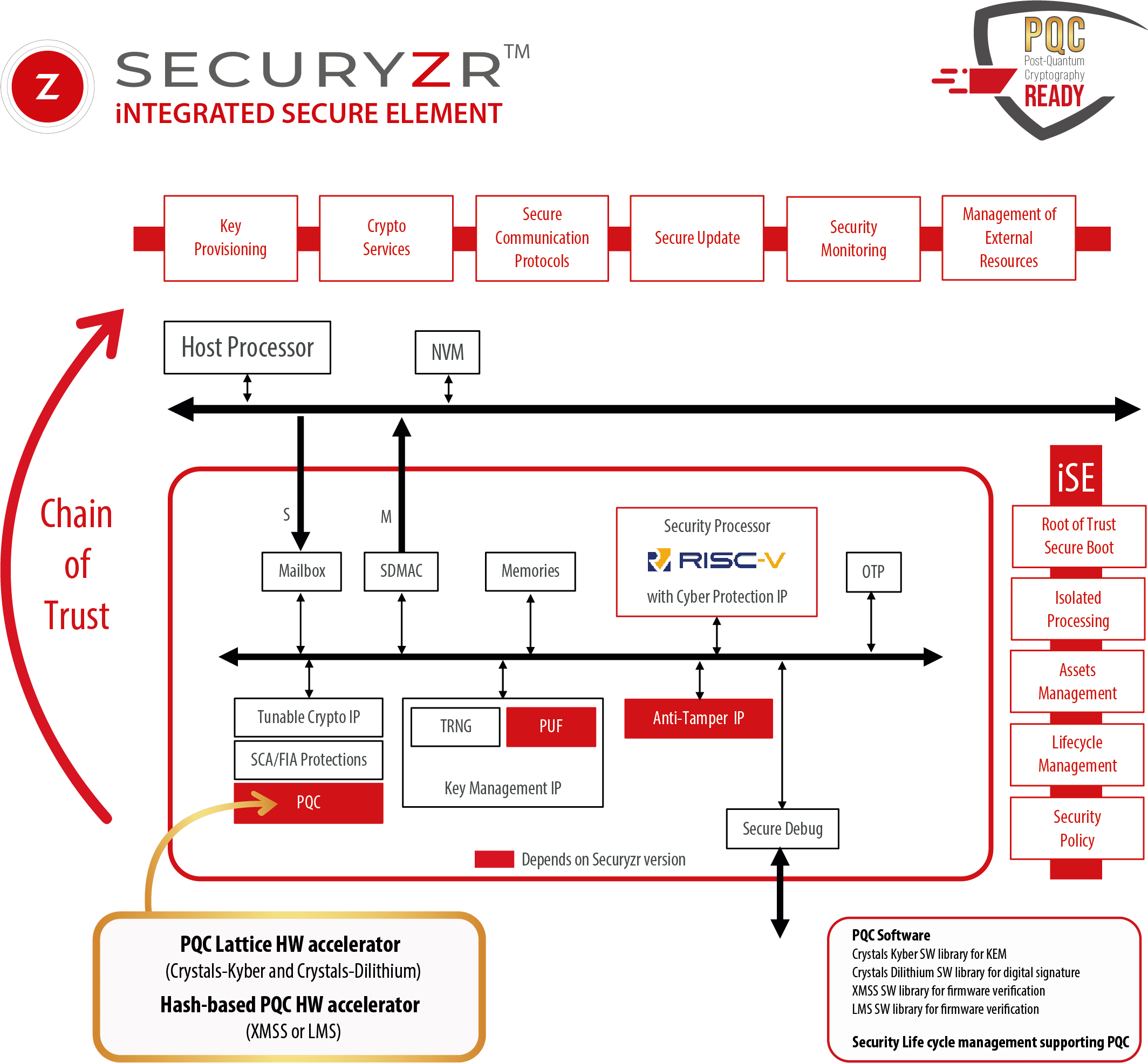
- SecuryzrTM integrated Secure Elements (iSE) supports both classical and post-quantum cryptography for dual-boot capability.
- The Software Cryptographic Library supports post-quantum cryptography using lattice-based and hash-based algorithms.
- A post-quantum cryptography IP which is composed a hardware accelerator (which is generic for all Lattice-based algorithm) and a software library which depends of the chosen algorithm (such as ML-KEM). This IP is illustrated in the below figure in the context of ML-KEM:

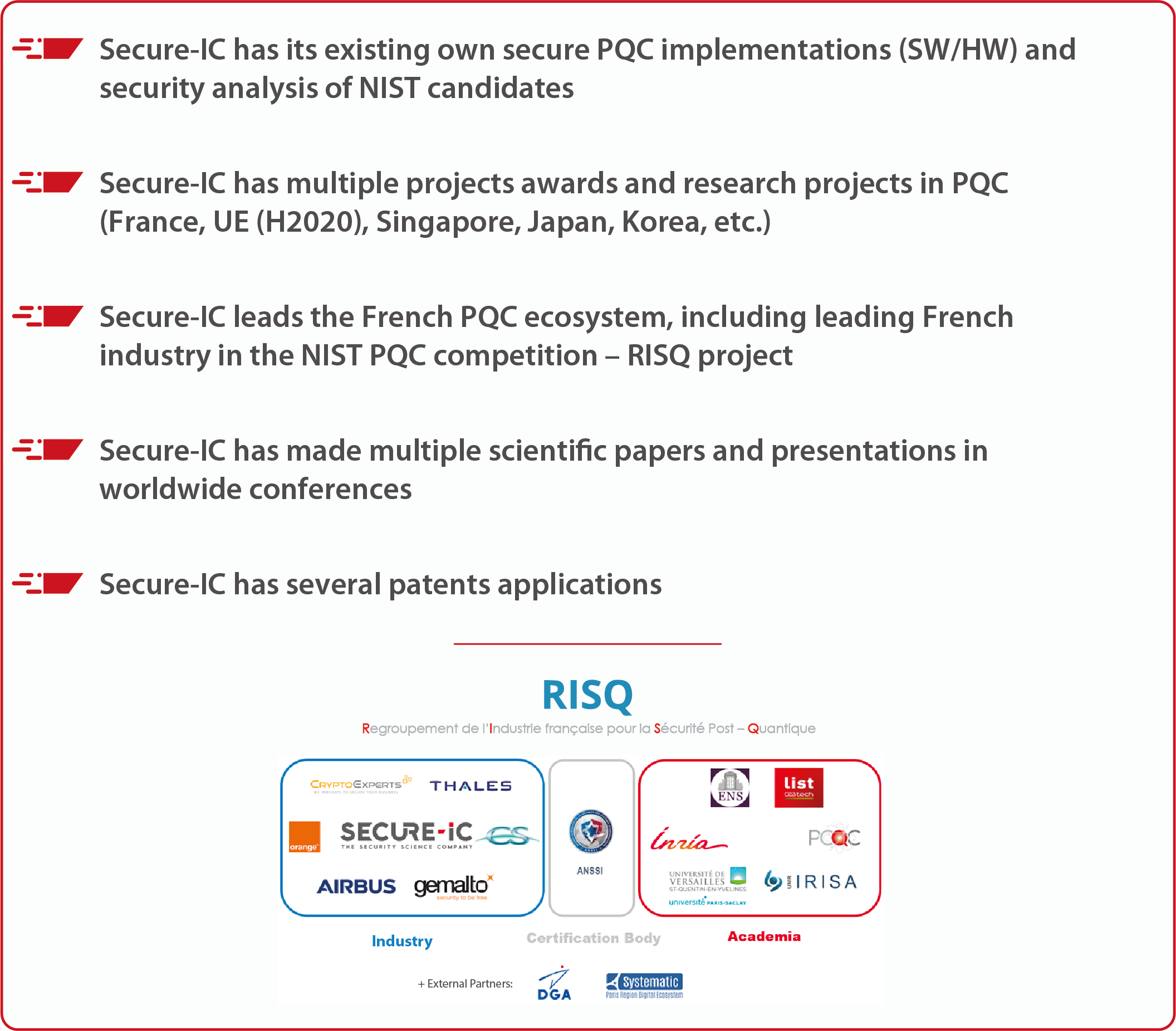
Secure-IC at the forefront of Post Quantum Cryptography for years
Secure-IC PQC implementations follow standards and market requirements


Secure-IC POST QUANTUM CRYPTOGRAPHY product offer

We offer a range of embedded security options to meet the unique needs of our customers, including post-quantum cryptography (PQC) solutions. From hardware-based PQC solutions to lifecycle management solutions, we have a variant that can provide the level of security required for your application.
Download our Post-Quantum Cryptography (PQC) White Paper
Post-Quantum Cryptography IP offers the following quantum-resistant features
- 512 and/or 768 and/or 1024-bit secret key length
- Implementation protected against Side-Channel Attacks (Key Generation and Key Decapsulation operations are sensitive):
- Simple Power Analysis (SPA)
- Differential Power Analysis (DPA)
- Differential Electromagnetic Analysis (DEMA)
- Correlation Power Analysis (CPA)
- Correlation Electromagnetic Analysis (CEMA)
- Hybrid hardware-software tunable solution
- Tunable in performance or power/area
- Performs Key Generation, Key Encapsulation and Key Decapsulation functions
- AMBA (APB, AHB, AXI) interface