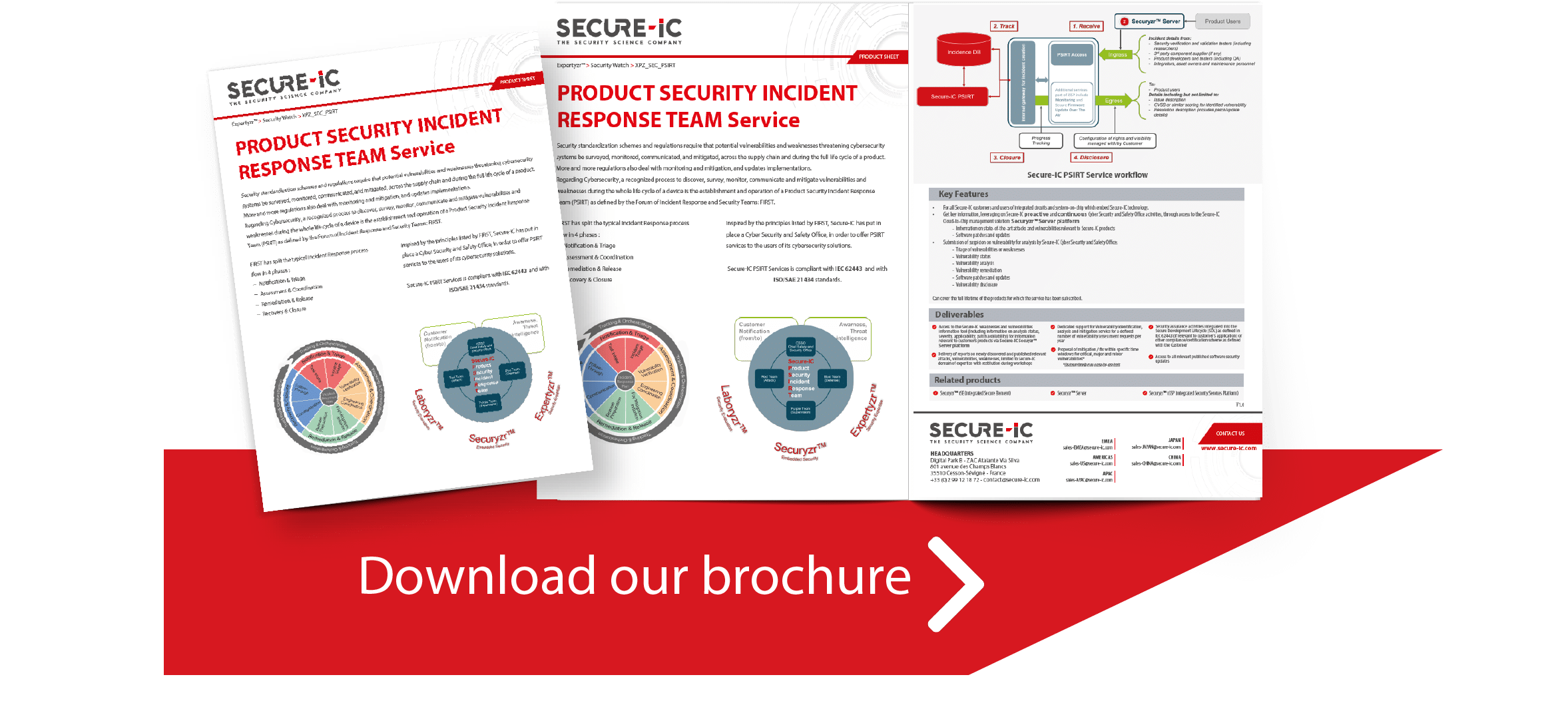
Product Security Incident Response Team Service
Security standardization schemes and regulations require that potential vulnerabilities and weaknesses threatening cybersecurity systems be surveyed, monitored, communicated, and mitigated, across the supply chain and during the full life cycle of a product.
Security standardization schemes and regulations require that potential vulnerabilities and weaknesses threatening cybersecurity systems be surveyed, monitored, communicated, and mitigated, across the supply chain and during the full life cycle of a product. More and more regulations also deal with monitoring and mitigation, and updates implementations.
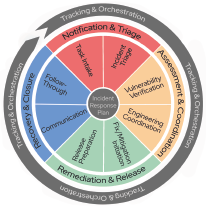
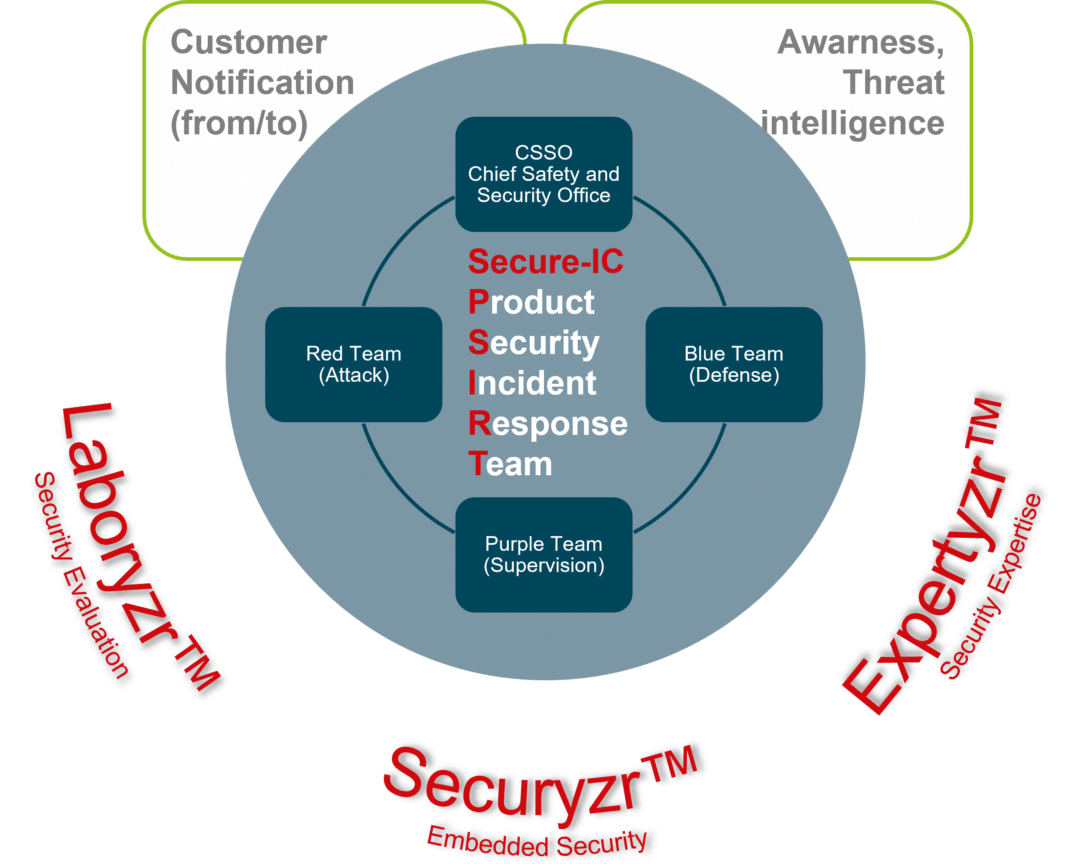
Regarding Cybersecurity, a recognized process to discover, survey, monitor, communicate and mitigate vulnerabilities and weaknesses during the whole life cycle of a device is the establishment and operation of a Product Security Incident Response Team (PSIRT) as defi ned by the Forum of Incident Response and Security Teams: FIRST.
Deliverables
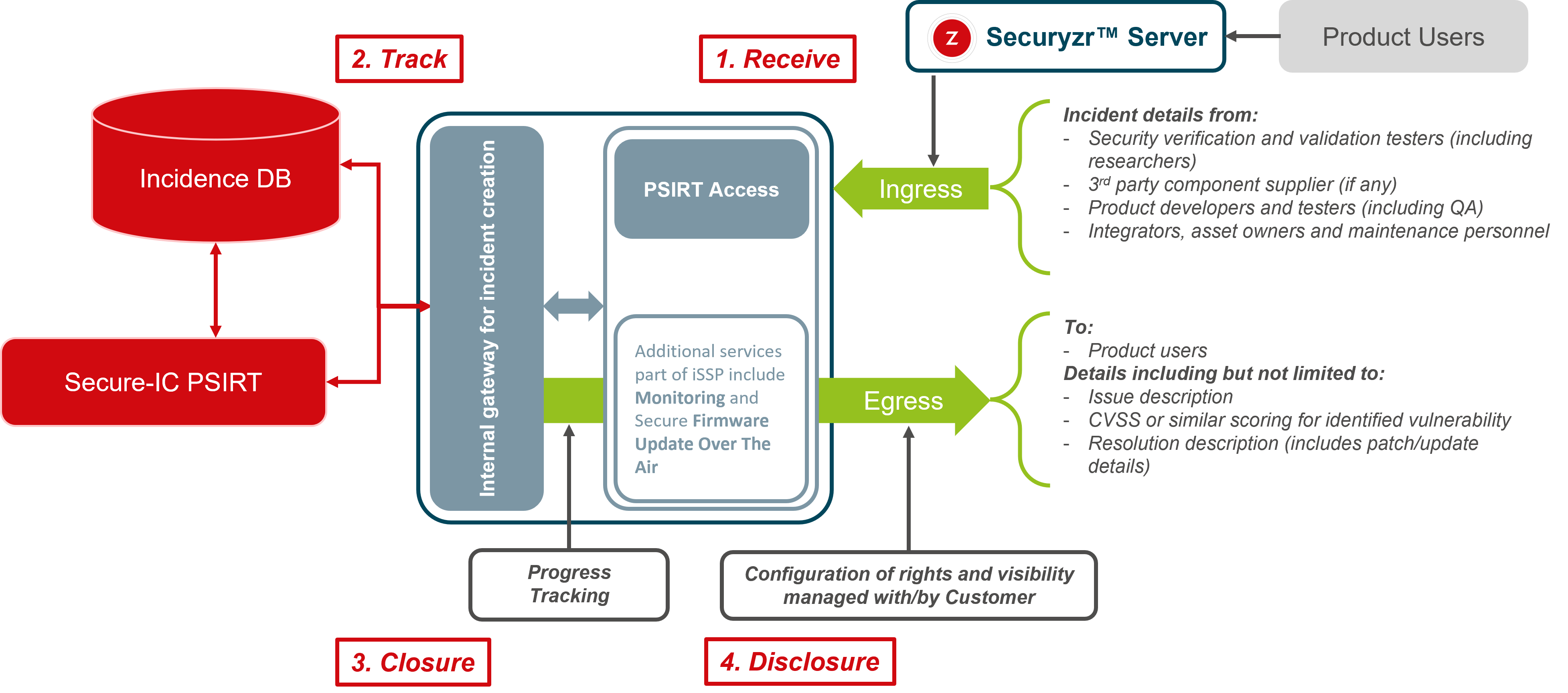
- Access to the Secure-IC weaknesses and vulnerabilities information tool (including information on analysis status, severity, applicability, patch availability) for information relevant to customer’s products via Secure-IC Secuyzr™ Server platform
- Delivery of reports on newly discovered and published relevant attacks, vulnerabilities, weaknesses,limited to Secure-IC domain of expertise with restitution during workshops
- Dedicated support for Vulnerability identifi cation, analysis and mitigation service for a defi ned number of vulnerability assessment requests per year
- Proposal of mitigation / fix within specifi c time windows for critical, major and minor vulnerabilities*
- Security assurance activities integrated into the Secure Development Lifecycle (SDL) as defi ned in IEC 62443 (if relevant to customer’s application) or other compliance/certifi cation scheme as defi ned with the Customer
- Access to all relevant published software security updates
*Disclosure timelines on a case-by-case basis
Related Products
- Securyzr™ iSE (integrated Secure Element)
- Securyzr™ Server
- Securyzr™ iSSP (integrated Security Services Platform