Securyzr™ iSE
Root of Trust solutions
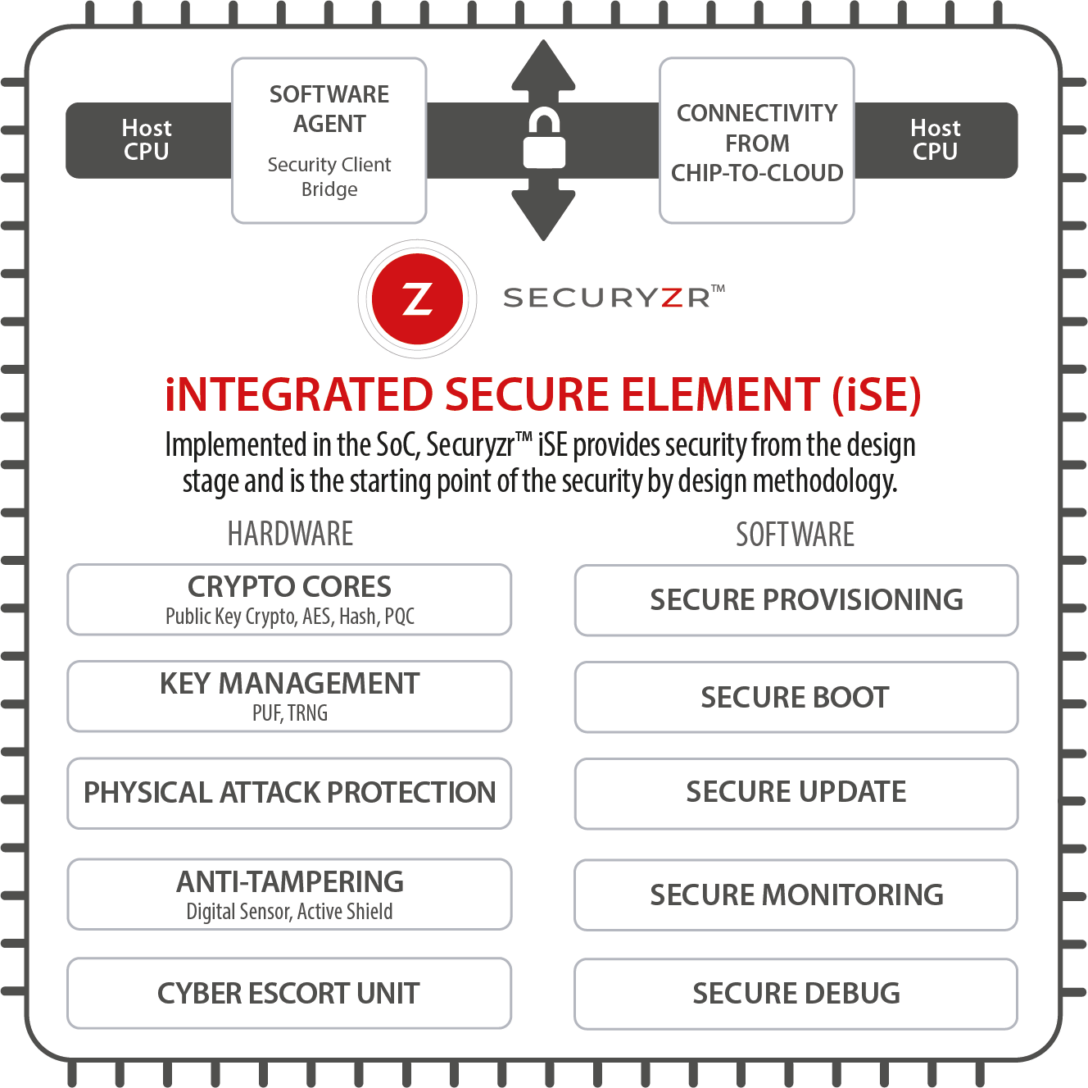
Securyzr™ integrated Secure Element (iSE) is Secure-IC Root of Trust solution. Embedded in the main SoC, it offers multiple services to its host system: provisioning, secure boot, secure firmware update, cryptographic services, multiple protections, etc.

Created to answer all ROOT OF TRUST needs
 |
Securyzr™ iSE is Secure-IC Root of Trust solution. Embedded in the main SoC, it offers multiple services to its host system: secure boot, key isolation, anti-tampering protection, etc. Thanks to its dual computation and strong isolation, it offers an additional layer of security compared to trusted execution environments. |
| HARDWARE | SOFTWARE | |||||
 |
Tunable Crypto |
|
 |
Secure Provisioning |
||
 |
Key Management |
|
 |
Secure Boot |
||
 |
Physical Attack Protection |
|
 |
Secure Update |
||
 |
Anti-Tampering |
|
 |
Secure Monitoring |
||
 |
Cyber Escort Unit |
|
 |
Secure Debug |
||
|
|
Secure any markets & applications
The SecuryzrTM iSE is a very efficient solution to enable any secure application on chip. The hardware module shielded from the main processor brings a high level of security. Also the hardware offloading of the cryptographic operations from the main processor to the SecuryzrTM iSE module guarantees a low power operation. The SecuryzrTM iSE module is tuned to the target application in terms of feature and performance.
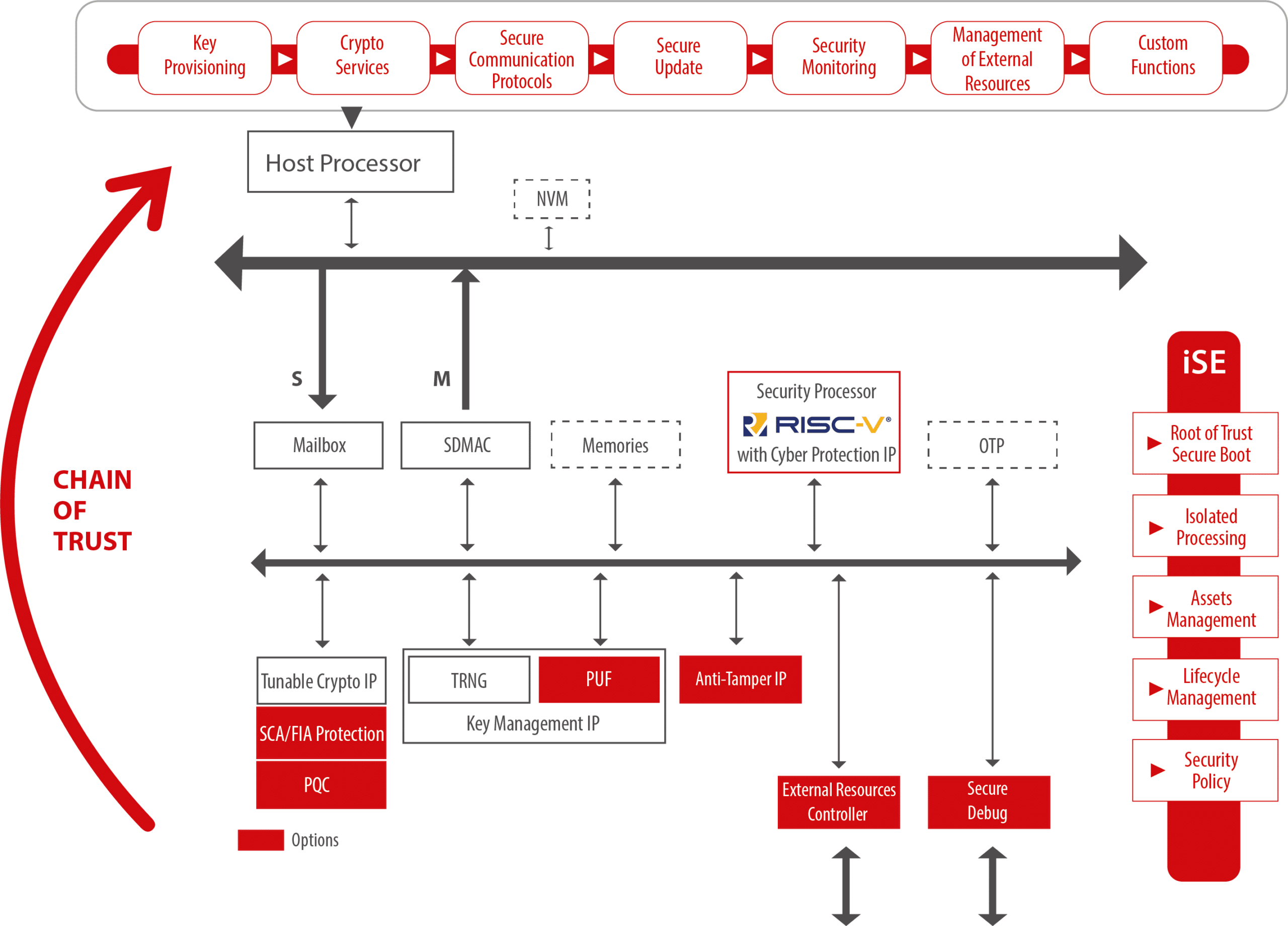
End-to-end security management platform from chip-to-cloud
A silicon root of trust with software support
The strength and versatility of software are also its weaknesses. Software has the ability to continually adapt, tune and improve but it is also corruptible and vulnerable to malicious software.
Writing secure software can be very expensive and time consuming, whereas hardware security is impervious to software attacks and is cheaper to implement.
Since silicon is physical and considered an immutable function, it cannot be changed as opposed to software, which can be compromised as it is stored in memory. Silicon guarantees that the information received is genuine and has not been altered. Having an immutable function propagates the root of trust throughout the system.
While software security cannot be considered as a standalone solution, it is still necessary to support hardware security. It is important to include both types in your security plan to cover all vulnerabilities.
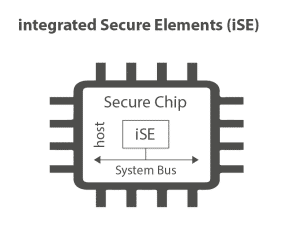
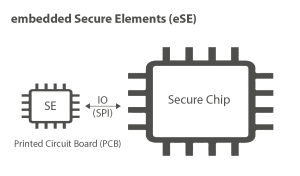
embedded vs integrated
embedded Secure Elements (eSE) and integrated Secure Elements (iSE) are different. On the one hand, eSE is said to be more complex as it possesses two chips but has limited resources and can be certified for a single application. On the other hand, iSE is customizable for each chip and each industrial application, it has a large amount of resources that can be shared with the host and hardware isolation; since they are integrated in the chip.
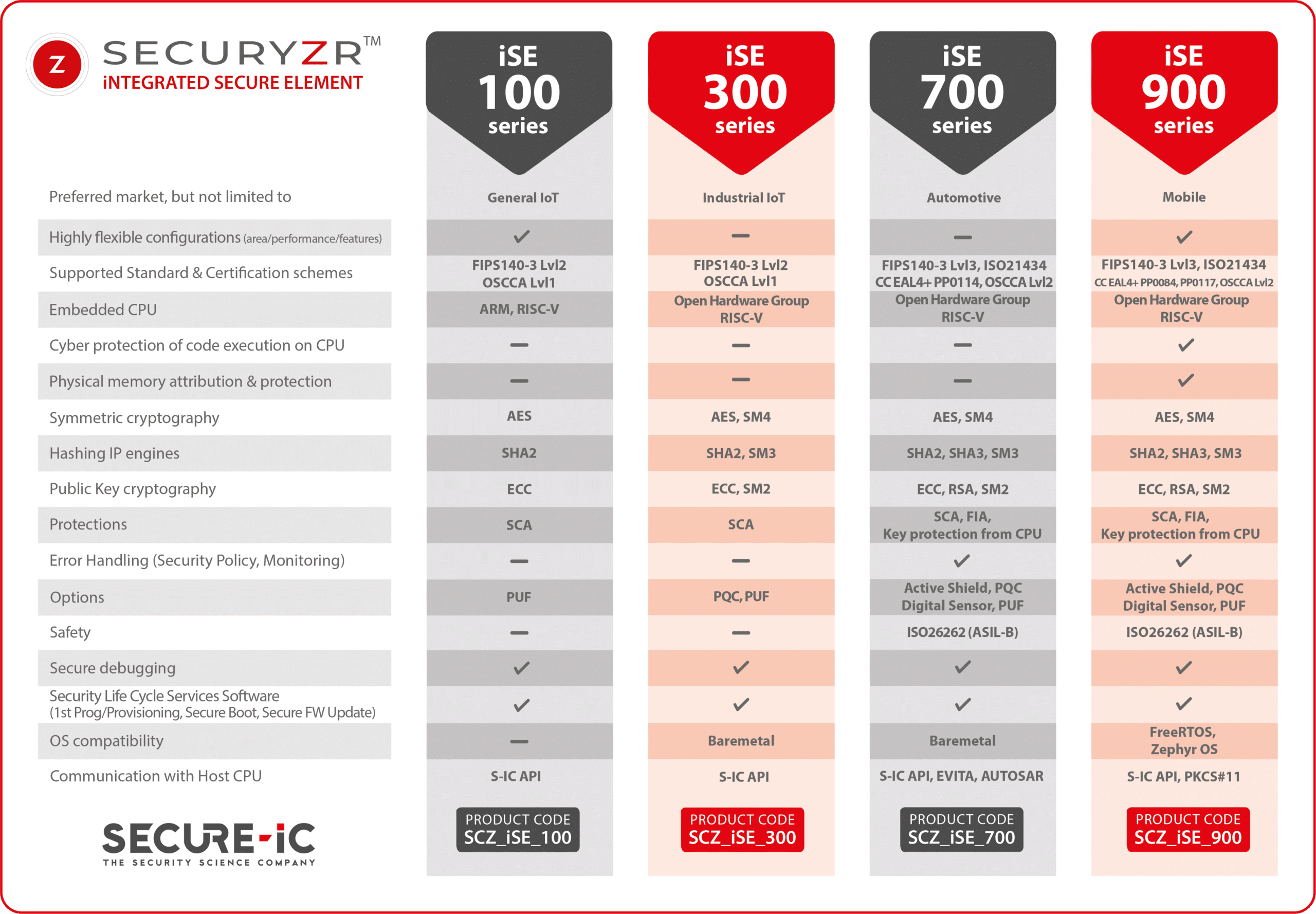
Certification Ready
Since security for industry is paramount, several standards exist. General certifications such as FIPS-140, OSCCA or Common Criteria are used in many different industries, including industrial IoT. As a security expert, Secure-IC supports companies in their certification objectives with operational consulting, trainings and services throughout their standardization process.
The first worldwide PQC READY secure solution from chip to cloud
 |
At Secure-IC we are at the forefront of PQC, meaning we are actively working on developing and implementing PQC technologies, and contributing to the advancement of the field. We are conducting research, creating new PQC algorithms, developing PQC-based products, and working with customers to integrate PQC solutions into their systems. |