Secure-IC leads the revision of ISO/IEC 17825

The International Organization for Standardization (ISO) is continuously working on the establishment of standards across the world to further develop a global framework applicable to all stakeholders from one industry to another.
In the context of Secure-IC, expert in embedded cybersecurity for connected objects, hard work is being conveyed every day to improve the security of systems across many industries such as the automotive, IoT, space, defense, cloud, and many others. With its strong Thought Leadership position, Secure-IC aims at participating in workshops organized by renowned and official public institutions, such as ISO, when developing standards or certifications by providing them with its expertise and resources.
One great example to illustrate the company’s commitment to this vast ecosystem that exists is the soon to be released ISO/IEC 17825 under its latest version. This was the result of a successful 4-year collaboration between NIST, CNITSEF, and Secure-IC. Indeed, the company led this work as part of the French ISO/IEC delegation (AFNOR) for which Secure-IC’s CTO & Co-Founder Sylvain GUILLEY was the lead editor.
“The update of the ISO/IEC 17825 International Standard brings two great news: first, this normative document will enable reproducible side-channel leakage detection. Second, I’m already happy to announce that compliant products will face significantly higher resistance against cyber-physical attacks.” – Sylvain GUILLEY, Co-founder and CTO of Secure-IC.
ISO/IEC 17825: What is at stake?
The revision aims at enhancing leakage detection by allowing the tester to tune false positive rate, hence making it more reliable for automation.
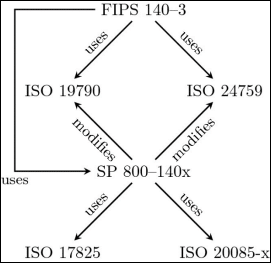
To better understand ISO 17825 and its use, one must learn the inner relationship that exists with previously published standards and global frameworks. Indeed, standards can refer to one another and be used as a reference, as demonstrated within this context.
ISO 19790
ISO 19790 refers to “the security requirements for a cryptographic module utilized within a security system protecting sensitive information in computer and telecommunication systems”. While data sensitivity can vary according to its context and application environments, four security levels were developed to assess the requirements specifically intended to maintain the security provided by a cryptographic module.
ISO 17825 is normatively referred as the “approved non-invasive attack mitigation test metric” inside ISO 19790 (appendix F) and has provisions for fitting into levels 3 and 4.
NIST FIPS 140
Going one level up, FIPS 140-3 are regulatory security requirements for cryptographic modules that rule whether an algorithm or a system is validated as conform or not for the protection of sensitive data or designated information.
ISO 19790 levels of security are directly used for the assessment of these algorithms within the NIST FIPS 140-3.
Secure-IC’s security solutions ISO/IEC 17825 enhanced
Secure-IC being a one-stop-shop for end-to-end security solutions, both evaluation tools and security IPs/subsystems are available for multiple applications and supported with expert services.
In this context, Secure-IC’s evaluation tools being Laboryzr™ has been upgraded to match with the new ISO 17825, ahead of its release publication.
Securyzr™ Cryptographic IP offering
Secure-IC classical and Post-Quantum Cryptographic offerings have been already validated to be leakage proof and are available for licensing. In addition to the algorithm implementation, Secure-IC embeds some SCA (Side Channel Analysis) countermeasures to strengthen the robustness of the cryptographic engines. Indeed, thanks to these countermeasures, our classical and Post-Quantum Cryptographic solutions comply and are certification ready with level 3 & 4 of FIPS 140-3.
Further information is available here
Laboryzr™ Evaluation tools
Secure-IC also implements the novel version of side-channel tests of ISO/IEC 17825 in its Laboryzr™ tools.
Advantageously, those tests can be carried out both pre-silicon & post-silicon stages and be applied to a wider range of use-cases including Post Quantum Cryptography.
This new version, implementing the possibility to tune the confidence level on false-positive or false-negative results, makes easier the automation of test campaigns and decisions using Laboryzr™ tools.