Securyzr™ MACsec Engine
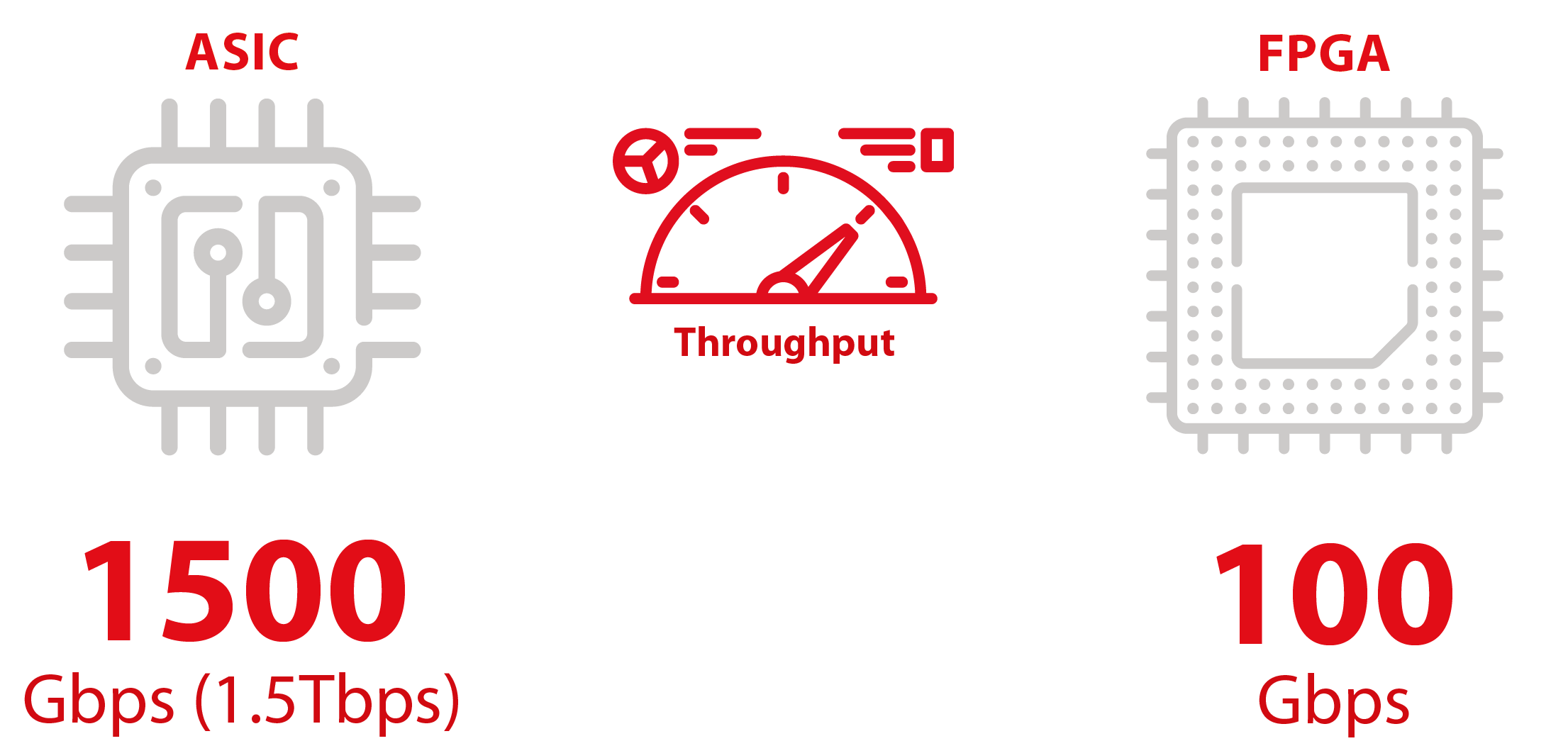
1.5 Tbps
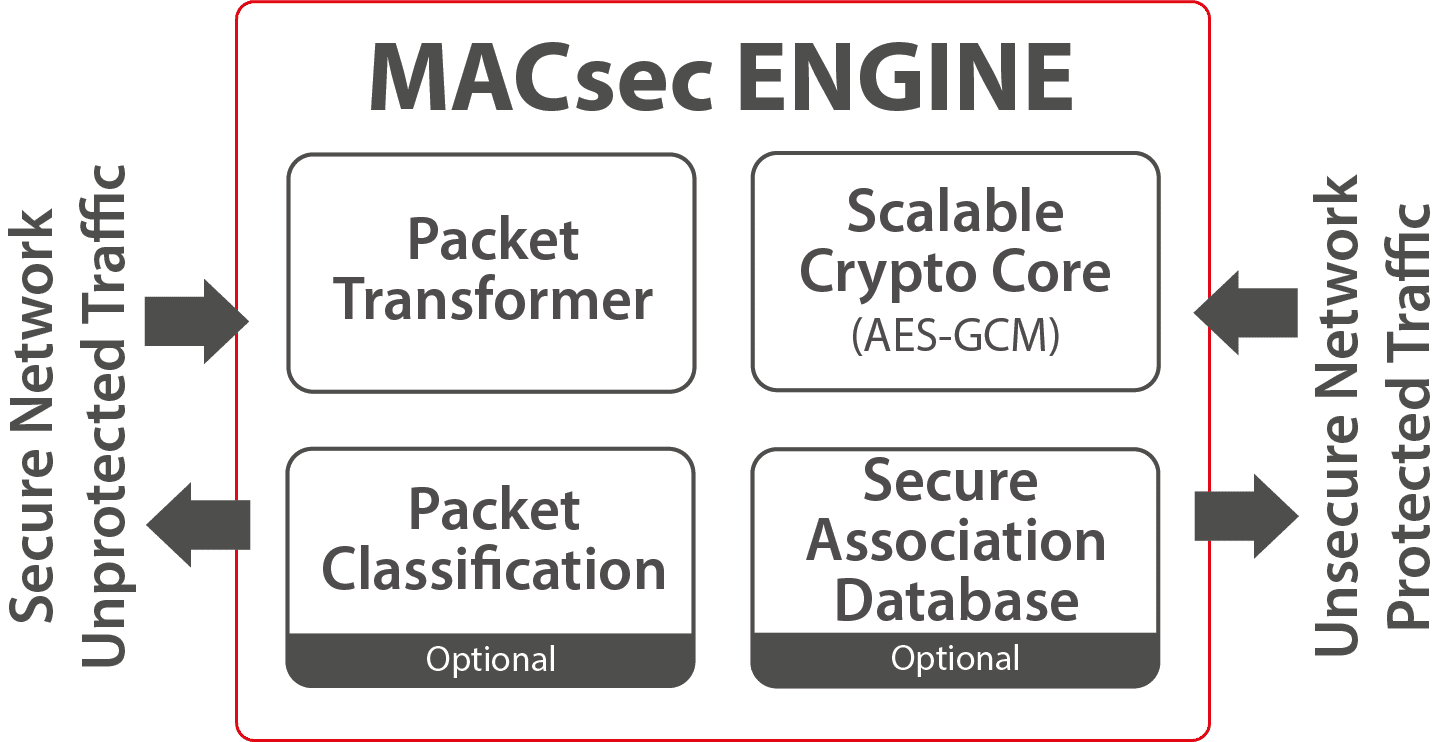
The Securyzr™ MACsec Engine, also known as Media Access Control Security, implements the latest IEEE 802.1AE specification, providing connectionless data integrity, data origin authenticity and confidentiality on OSI layer 2.
The scalable architecture provides low-latency, line rate acceleration of frame encapsulation, encryption and replay protection. The multi-channel structure makes the engine extremely suitable for use in switches, enabling per-port security with a single IP instantiation. Integration options with either performance or area-optimized AES-GCM IP cores enables a high level of scalability enabling unrivalled trade-off possibilities between throughput, area and latency.
At its very core, the MACsec Engine is completely technology-agnostic and can be integrated in a wide range of FPGA and ASIC technologies. On FPGA, the engine can use vendor-specific optimizations to reach very high throughput goals.
| Low Latency Optional cut-through design helps reaching timing targets for latency-critical applications |
No software intervention Can be implemented fully in hardware without any software intervention |
|||||
| Replay protection Offloading replay protection and packet number management reduces the strain on the CPU even more |
Line rate acceleration Highly efficient cryptographic cores enable reaching line rate processing, even for 64 byte packets |

Features
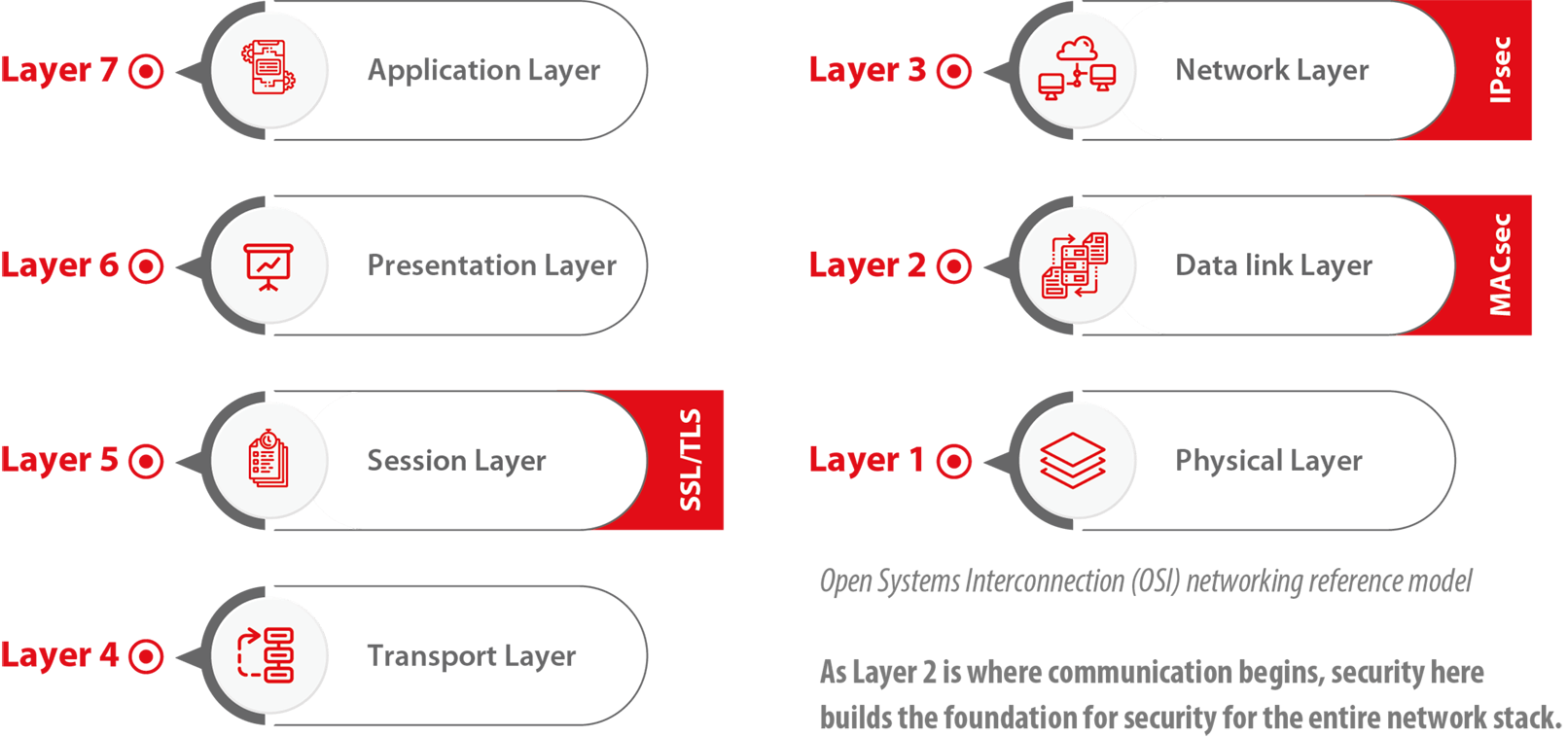
MACsec is the foundation for any network security
There are three common network security protocol standards:
| MACsec Regulating the traffic of frames between two physical machines, regulated by the MACsec protocol of layer 2. |
||
| IPsec Checking and ordering the routed packets, done by the IPsec protocol in layer 3. |
||
| TLS (SSL) Checking the authenticity of the incoming requests and setting up the encryption/decryption. This is the SSL/TLS handshaking of layer 5. |
MACsec provides Layer 2 (the data link layer – OSI) security allowing it to safeguard network communications against a variety of attacks including intrusion, denial of service and eavesdropping. These attacks exploit vulnerabilities in the data line layer and often it will not be detected or prevented by higher layer security protocols. Therefore, MACsec provides the basis on which a network security architecture can be built.
Free white paper
HOW SMART & SECURE HARDWARE
CAN BOOST YOUR DATA CENTER
High-performance IP blocks to offload network and security processing
Cloud computing is ramping up like never before. New host applications are routinely designed to serve millions of clients, and each of these clients expects high-speed service, minimal latency, and tight security.
Learn more about the key components to boost your data center:
• Record-breaking MACsec performance (up to 1.5Tbps)
• The fastest SSL/TLS handshaking engines in the industry
• …and much more

The first worldwide PQC READY secure solution from chip to cloud
 |
At Secure-IC we are at the forefront of PQC, meaning we are actively working on developing and implementing PQC technologies, and contributing to the advancement of the field. We are conducting research, creating new PQC algorithms, developing PQC-based products, and working with customers to integrate PQC solutions into their systems. |