Securing the security – Physically Unclonable Function (PUF)

With the rapid expansion of the IoT technologies which have a key role in our everyday lives, security is now becoming more and more important. Indeed, a few years ago, digital security was simple and used on electronic devices dedicated to that purpose, such as bank cards or payment terminals but today it has become much more complicated than that. Security cannot be an after-thought when dealing about new technologies. The increase of the use of information technology has led in more and more sensitive data moving from system to system and as a result, the safety requirements to protect this data have also increased. Large amounts of tools have been created to meet those safety requirements such as ASICs, microcontrollers, SOCs embedding hardware cryptographic accelerators or software cryptographic libraries.
At the center of any device’s security architecture resides a cryptographic root key. From this root key, additional keys can be derived for authentication, software validation or encryption of sensitive data. Any device connected to a network or carrying something of value (such as data or IP) must use these keys to operate securely. These keys are the foundation of trust for all devices and should never fall into malicious hands that could be looking to steal sensitive information, intellectual property or even to disrupt the system.
Since the invention of automated reverse engineering and the development of fault analysis techniques, physical attacks are more feasible than ever. It is therefore important not to compromise physical protection when securing cryptographic keys.
Storing cryptographic keys in non-volatile memory (like OTP, EEPROM or Flash) and implementing layout countermeasures or obfuscations have always been the usual way to design secure key storage. Some more robust solutions rely on memory encryption through a master key, but then, who protects the master key? In addition, obfuscation methods require highly specialized know-how and those solutions are scarce in the market.
Physically Unclonable Functions (PUFs) are functions implemented in devices that are produced or configured with the security objective that random fluctuations in the production process lead to different behaviors and are hard to reproduce physically, to produce secure and unique sets of values.
A PUF is usually enrolled at the provisioning level, when the chip is configured and programed (enrollment operation) which may involve the generation of help data (to correct error of noisy responses) and then it may issue a unique ID or key upon request (post-enrollment query operation or key rebuilding procedure).
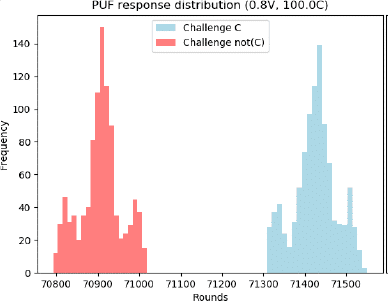
As in any product, a PUF is an additional feature that is expected to be reliable down to the smallest fault. Secure-IC’s PUF offers a reliable and steady feature in SecuryzrTM. Using process–volume temperature (PVT) empirical tests, analog simulations at pre-silicon stage and post-silicon ageing accelerations; the PUF has stayed reliable (as can be seen on the figure below).
For a PUF to be even more reliable, it has also to be unpredictable, which means that it must have good entropy on the results otherwise issues can occur and render the product vulnerable to attacks. Secure-IC has taken this into account and provided an unpredictable PUF.
What does Secure-IC offer in terms of PUF protection?
By using a PUF in SecuryzrTM, security is ensured by an integrated element and this is valuable for the SoC. It can also offer a simplification of the chip interfaces, as no key has to be injected into the component.
By construction, the key disappears when the power is turned off, but it can be regenerated internally with a uniqueness to each chip Secure-IC offers and by keeping the unpredictability of the chip intact.
A PUF can be useful in many different situations as it is a very versatile solution:
- Secure boot: The PUF generates the Master key to check for the authenticity of the firmware. A subsequently authenticated external Flash can be used as a secure memory
- Configuration and activation of a chip from the cloud
- Challenge-Response Protocol for authentication
- Unforgeable Identification Device
- Unique seed for a deterministic random bit generator
- Root key to generate secondary keys thanks to an appropriate key derivation function (KDF)
Most of the time, PUF can be used for cryptography and authentication cases as it provides a secret key.
Secure-IC’s PUF has been experimentally validated to provide a reliable, safe and highly entropic security feature. And it continues to undergo further tests and security requirements such as ISO 20897 to make it increasingly safe and reliable.
Do you have questions on this topic and on our protection solutions? We are here to help.